New ransomware decryptor “White Phoenix”
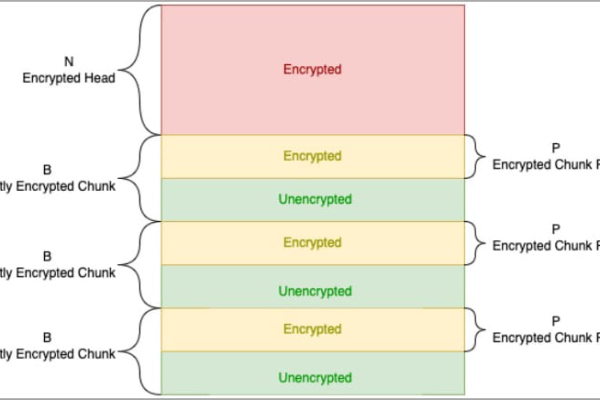
A new ransomware decryptor known as ‘White Phoenix’ allows victims to partially recover files encrypted by ransomware strains that use…

A new ransomware decryptor known as ‘White Phoenix’ allows victims to partially recover files encrypted by ransomware strains that use…
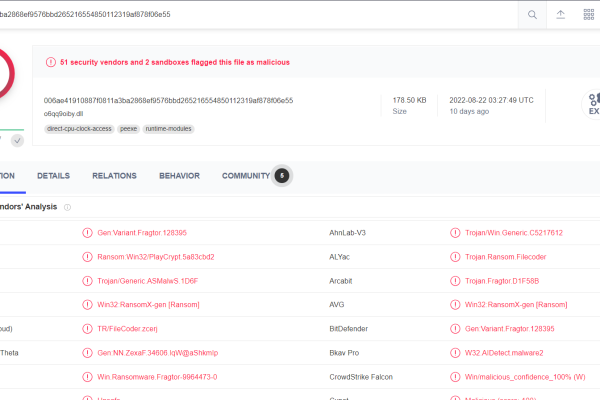
PLAY CTI PLAY Ransomware (aka PlayCrypt) campaigns have been active since at least mid-July 2022. Up to five ransom notes…
LockBit CTI On 4 February 2022, the FBI issued FLASH security advisory on Indicators of Compromise (IOCs) associated with LockBit…
Babuk Ransomware Overview This is the report for the new Babuk Ransomware that recently appears at the beginning of 2021….