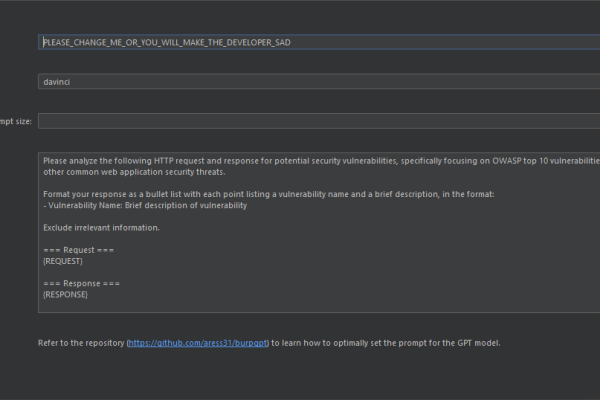
BurpGPT – ChatGPT Powered Automated Vulnerability Detection Tool
Cyber Security News discovered “BurpGPT,” a new ChatGPT powered vulnerability discovery tool that assists security researchers in detecting flaws that…

Cyber Security News discovered “BurpGPT,” a new ChatGPT powered vulnerability discovery tool that assists security researchers in detecting flaws that…
Do you want to learn how to hack web browsers yourself? If that’s the case, you’re in luck! In this…

A skilled scanner will be able to answer these questions. Today, we’ll look at three tools: Nmap, Nessus, and Greenbone…
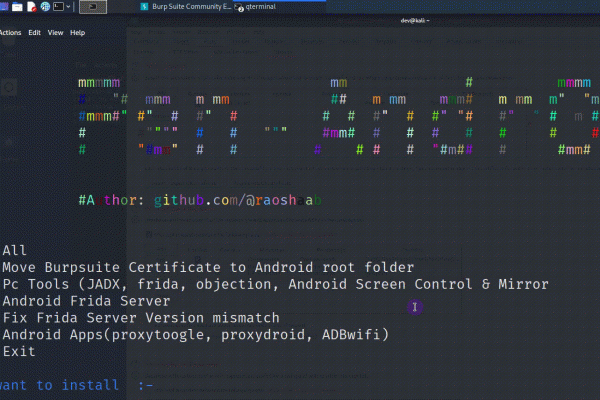
The Pen-Andro Script will automate the process of installing the essential tools and tasks for Android pentesting, such as moving…
“PentestGPT” is a new ChatGPT-powered penetration testing tool that assists penetration testers in automating their pentesting activitie. PentestGPT was uploaded…

Penetration testing, or “pentesting,” is an essential process to ensure the security of iOS devices and applications. In this iOS…
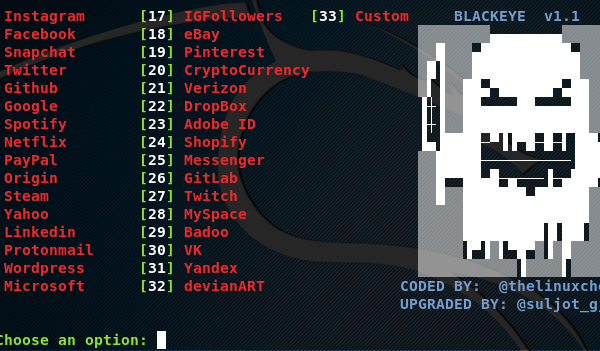
BLACKEYE is a LAN phishing tool that can clone more than 30 networks templates to generate the phishing pages. Some…

Kali Linux commands cheat sheet. All basic commands from A to Z in Kali Linux has been listed below. A…

In this Android penetration testing cheatsheet, we will provide you with a list of the most crucial commands and tools…

What Is Metasploit? Metasploit is a popular open-source framework for creating, testing, and deploying exploits. It is used by hackers…