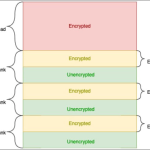
In a recent cybersecurity investigation, experts have identified several widely-used Chrome extensions that are leaking sensitive user data—including browsing history, device identifiers, and behavioral patterns—over unencrypted HTTP connections. This transmission of data without encryption leaves users dangerously exposed to interception and tampering.
🔍 Detailed Findings
Cybersecurity researchers discovered that some of the most downloaded Chrome extensions are engaging in the following:
1. Transmitting Browsing History in Plaintext
- SEMRush Rank and PI Rank transmit URLs of visited websites to
http://rank.trellian.com - This allows third parties to build profiles of user behavior and interests with ease
2. Unsafe VPN Practices
- Browsec VPN, marketed as a privacy-focused service, leaks user data upon uninstall to
http://api.browsec.com - Transmits identifiers such as extension version, platform type, and user ID without encryption
3. Invasive Tracking
- MSN Homepage & New Tab extensions send telemetry data to
http://g.ceipmsn.com - Leaked data includes:
- Unique machine ID
- Country
- Language settings
- Chrome profile identifier
4. Password Manager Unsafe Behavior
- DualSafe Password Manager contacts
http://stats.itopupdate.com - Sends extension metadata, locale settings, and user metrics in unencrypted form
🧨 Hardcoded API Keys & Credentials
Some extensions also ship with hardcoded API credentials, making them vulnerable to abuse:
- AVG Online Security and SellerSprite expose Google Analytics secrets in public JavaScript
- Equatio includes a Microsoft Azure API key used in its speech-to-text feature
These static credentials can be harvested by attackers to:
- Access premium APIs without authorization
- Bypass rate limits
- Inflate cloud service costs
- Launch abuse campaigns using valid tokens
⚠️ Security Risks
When data is transmitted over HTTP instead of HTTPS:
- Attackers on the same network (e.g., public Wi-Fi) can intercept the traffic
- Data may be modified in transit (e.g., injecting malware or redirecting links)
- Exposes organizations to compliance and legal issues (especially under GDPR/CCPA)
✅ What You Should Do
🔐 If You’re a User:
- Audit your Chrome extensions
- Remove anything not critical or verified by trusted vendors
- Use browser security tools that monitor extension behavior
🛠️ If You’re a Developer:
- Never use HTTP endpoints; always enforce HTTPS
- Avoid embedding sensitive keys/secrets in front-end code
- Validate all remote APIs against secure schemas
📰 References:
⚡ Stay aware, stay secure.
Every extension you install is a potential window into your digital life. Choose wisely.