Cybersecurity researchers have uncovered a sophisticated malware campaign that leverages fake software installers, masquerading as popular tools like LetsVPN and QQ Browser, to distribute the Winos 4.0 malware framework.
🧩 The Catena Loader: A Stealthy Delivery Mechanism
The campaign, first identified by Rapid7 in February 2025, employs a multi-stage, memory-resident loader known as Catena. This loader utilizes embedded shellcode and configuration-switching logic to stage payloads like Winos 4.0 entirely in memory, effectively evading traditional antivirus tools.
“Once installed, it quietly connects to attacker-controlled servers—mostly hosted in Hong Kong—to receive follow-up instructions or additional malware,” noted security researchers Anna Širokova and Ivan Feigl.
🎯 Targeted Regions and Threat Actors
The attacks predominantly focus on Chinese-speaking environments, indicating a strategic approach by a highly capable threat actor. The Winos 4.0 malware, also known as ValleyRAT, was initially documented by Trend Micro in June 2024 and has been linked to a threat cluster tracked as Void Arachne or Silver Fox.
🕹️ Evolving Tactics: From Browsers to Gaming Applications
Subsequent campaigns have expanded their reach by leveraging gaming-related applications, such as installation tools and optimization utilities, to trick users into installing the malware. A notable attack wave in February 2025 targeted entities in Taiwan through phishing emails impersonating the National Taxation Bureau.
🛠️ Technical Breakdown: Infection Chain and Persistence
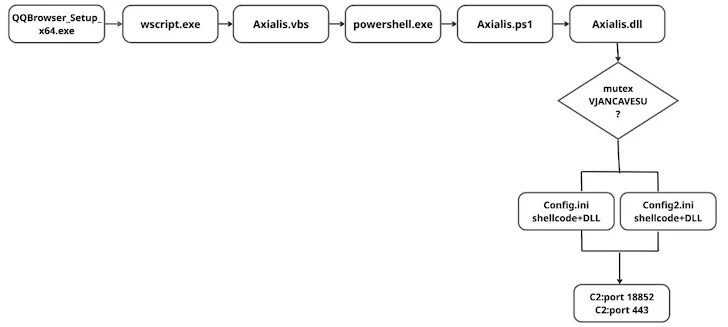
The infection chain, dubbed Catena, involves:
- Trojanized NSIS installers bundled with signed decoy applications.
- Shellcode embedded in
.inifiles. - Reflective DLL injection to maintain persistence covertly.
The malware communicates with hard-coded command-and-control (C2) infrastructure over TCP port 18856 and HTTPS port 443. Persistence is achieved by registering scheduled tasks that execute weeks after the initial compromise.
🧠 Language Checks and Tactical Shifts
Interestingly, the malware includes a check for Chinese language settings on the system. However, it proceeds with execution even if the condition isn’t met, suggesting an unfinished feature. In April 2025, Rapid7 observed a tactical shift, with changes in the Catena execution chain and added features to evade antivirus detection.
🔍 Indicators of Compromise (IOCs)
Security professionals should be vigilant for the following IOCs:
- NSIS installers masquerading as legitimate software.
- Unusual scheduled tasks set to execute weeks post-installation.
- Network traffic directed to C2 servers over uncommon ports like 18856.
🛡️ Mitigation Strategies
To protect against such threats:
- Verify software sources before installation.
- Implement behavioral analysis tools to detect memory-resident malware.
- Regularly update antivirus and endpoint protection solutions.
- Educate users about the risks of downloading software from unverified sources.
📚 Further Reading
👉 Hackers Use Fake VPN and Browser NSIS Installers to Deliver Winos 4.0 Malware
Stay informed and stay safe. Cyber threats are evolving—ensure your defenses evolve too.